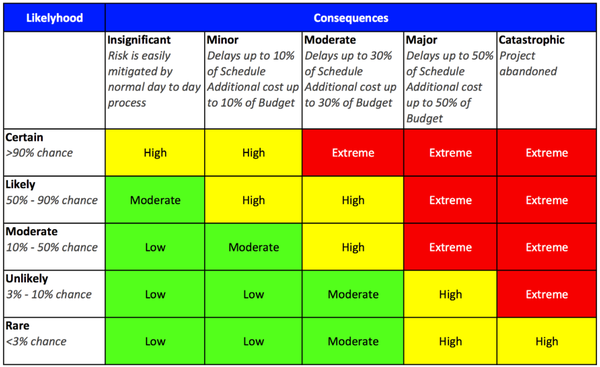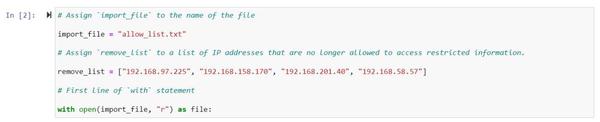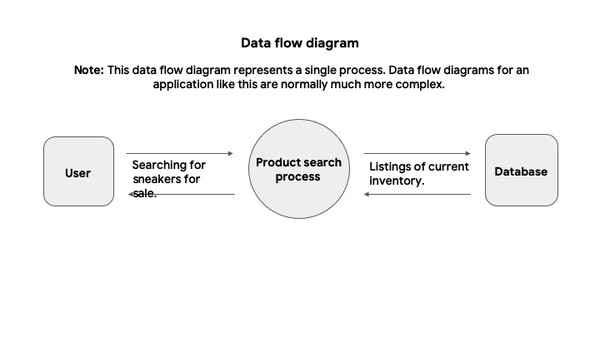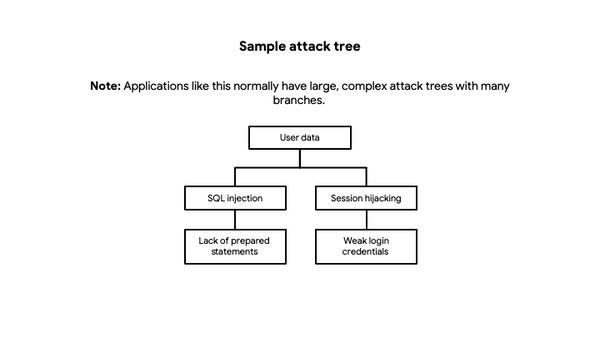


Hello, I'm Joseph LaCount, and I'm excited to share my cybersecurity journey with you. As a tech enthusiast and a dedicated learner, I've completed a comprehensive cybersecurity program, equipping me with a diverse skill set to navigate the ever-evolving world of information security. This portfolio serves as a showcase of my knowledge, accomplishments, and the projects I've worked on. I have a passion for cybersecurity, and I'm ready to apply my skills to safeguard the digital world. Explore my projects and experiences to get a glimpse of my capabilities and dedication to the field. Let's connect and explore the world of cybersecurity together!

I'm Joseph LaCount, a passionate and results-driven technology enthusiast with a strong background in web development, IT support, and a deep commitment to cybersecurity. As a junior front-end web developer, I've honed my skills in creating engaging online experiences. Simultaneously, I've gathered practical IT support experience, fostering a comprehensive understanding of user needs and technical problem-solving. My journey has led me to operate my web design company, Grace Coding, where I've been crafting high-end web and graphic design solutions for clients from diverse industries.
Currently, I am enrolled in LACC taking coursework to obtain my AS in Cybersecurity with the intent to transfer to CSUSM to finish with s BS in Cybersecurity. I have successfully attained my Google Cybersecurity Certificate through Coursera, a valuable addition to my skill set that has equipped me with the tools to defend against digital threats. My experience extends to actively contributing to projects like Delete The Divide with ISD of Los Angeles County, advocating for digital equity, and offering IT support to the community. I've even ventured into the renewable energy sector as a Rework Technician, applying my IT and data analysis skills.
My core strengths include effective communication, problem-solving, and a strong penchant for collaboration. In every role, I strive to apply my skills for the betterment of projects and organizations. As an individual who is ever-curious and driven to contribute to the rapidly evolving world of cybersecurity, I'm excited to continue my journey by protecting digital assets and creating robust, secure online environments for organizations.
I am also a member of the HTCIA (High Technology Crime Investigation Association), a leading professional organization dedicated to investigations involving advanced technology.