31st October 2023
Risk Register Sample Risk Matrix
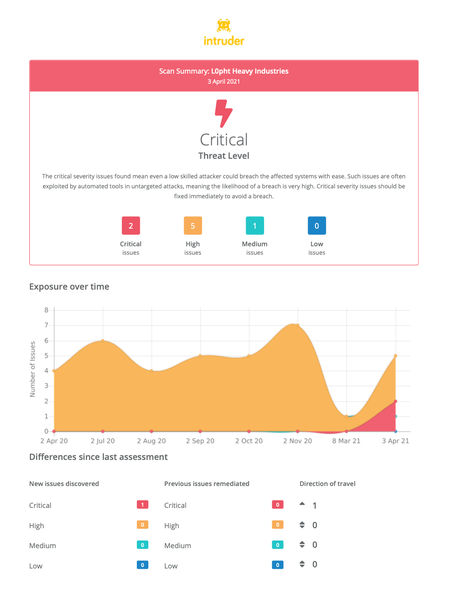
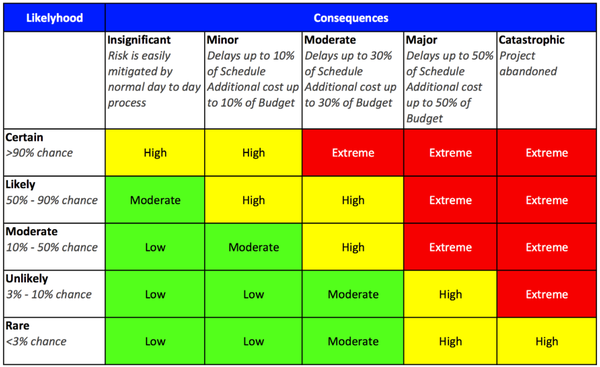
In the operational environment of a coastal bank, where stringent financial regulations demand data and fund security, this risk register identifies potential risks to various assets, including funds, customer data, financial records, and physical security. These risks encompass scenarios such as business email compromise, user database compromise, and financial record leakage. The register assesses each risk's likelihood, severity, and priority, highlighting vulnerabilities within this unique operating context. This tool serves as a crucial instrument in proactively managing and mitigating potential security threats in a complex banking environment.